The respected Comrade
"The sector of science and technology should conduct a vigorous campaign to surpass the cutting edge."
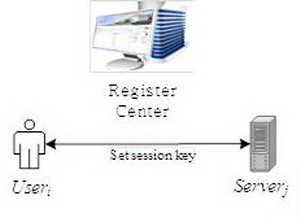
Research on authentication key agreement for secure data communication between users and servers in multi-server environment is being conducted in the Faculty of Information Science,
In a multi-server environment, authentication key agreement is a method of setting the session key necessary for encryption and decryption, while allowing mutual authentication between the user and the server.
Recently, the authentication key agreement has become a more important research area, as services are being implemented in multi-server environments such as Internet of Things, P2P, cloud computing, WSN, etc.
For authentication key agreement, cryptography techniques (such as public key encryption and symmetric key encryption) and authentication techniques (such as knowledge-based authentication, property-based authentication and biometric–based authentication) are being applied.
Recently, a further research has been made on preserving anonymity, encryption of exchanged messages, and lightweight communication to improve the performance of authentication key agreement.
We have studied mutual authentication key agreement in a multi-server environment with improved security properties using pseudo-identifiers.
We have proposed authentication key agreement method, by which users are authenticated by verifying user's password, smart card and biometric, and perfect-forward security is satisfied by encrypting the message exchanged between users with pseudo-identity and updating it each time.
The proposed method has proved to satisfy the security requirements of mutual authentication, anonymity, untraceability, and perfect-forward security, be secure against various attacks such as impersonate attack, smart card stolen attack, man-in-the-middle attack, password guessing attack, and have traffic and computation complex for key agreement superior to the previous method.
The results of the above study were published under the title of "Cryptanalysis and improved mutual authentication key agreement protocol using pseudo-identity" (https://doi.org/10.1371/journal.pone.0271817) in PLOS ONE (2022, 17 (7), e0271817).